Description
In this video I show how to finish recreating the popular SLMail exploit!
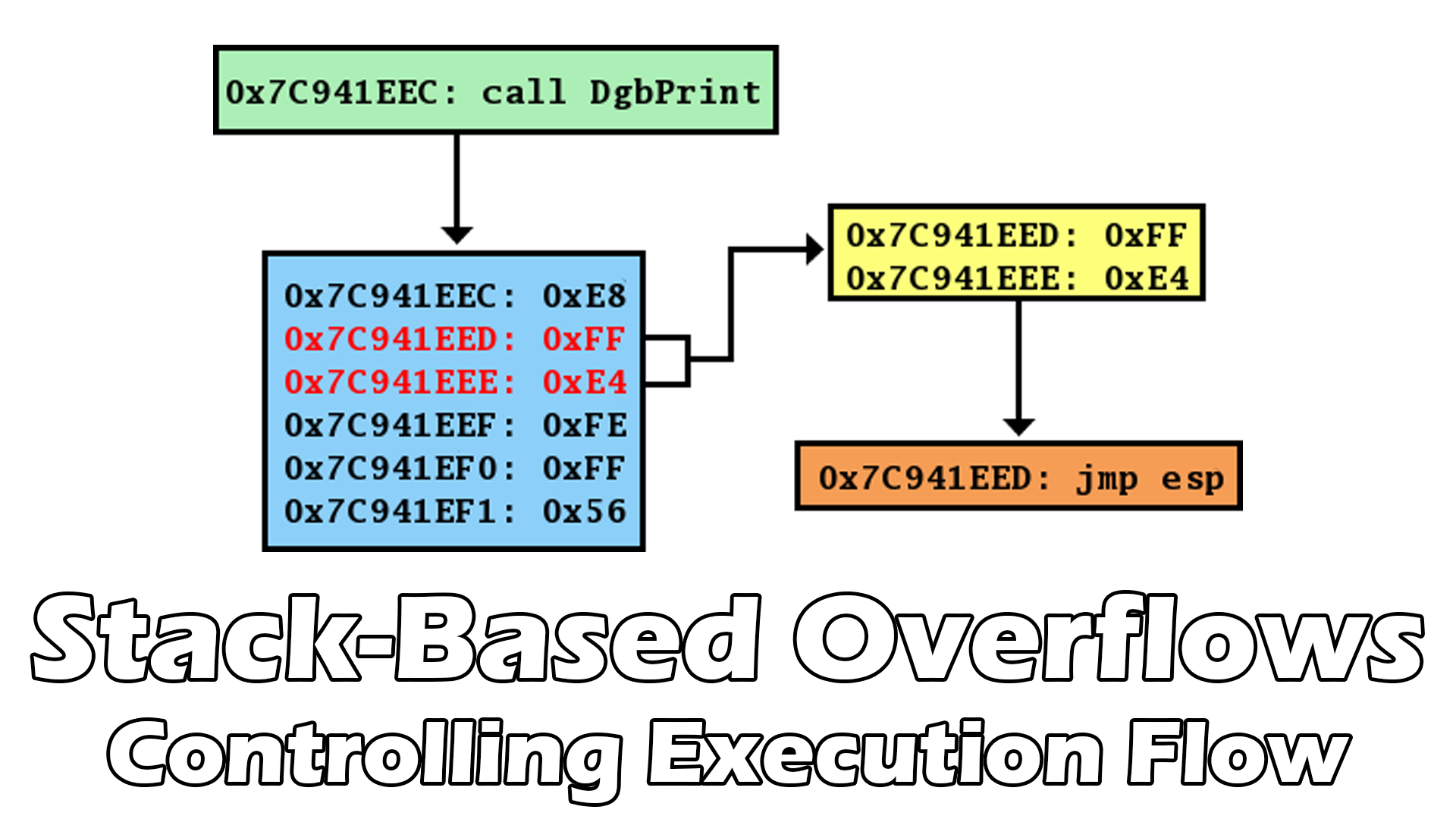
This video is the final part of the stack-based overflow mini-series. The first part can be found here:
https://www.youtube-nocookie.com/watch?v=ad9I4y88icM
Topics covered:
– NOP & INT3 CPU Instructions
– Finding bad (i.e. filtered) characters
— The “Byte Array” function
— The “Compare” memory function
– Generating shellcode with msfvenom
– Configuring and using the metasploit multi/handler
– Reconfiguring the Windows firewall to allow incoming connections to SLMail
– Using NMAP to scan a local subnet (/24) for live hosts and identifying the SLMail host
– Brief Post Exploitation with Metasploit
— Upgrading basic shells to meterpreters
— Obtaining RDP access using post modules and rdesktop
Stay tuned and subscribe for more upcoming videos showing actual hacks!
Twitter: @CrazyDaneHacker
Facebook: https://www.facebook.com/crazydanishhacker
Patreon: https://www.patreon.com/crazydanishhacker

Recent Comments