Description
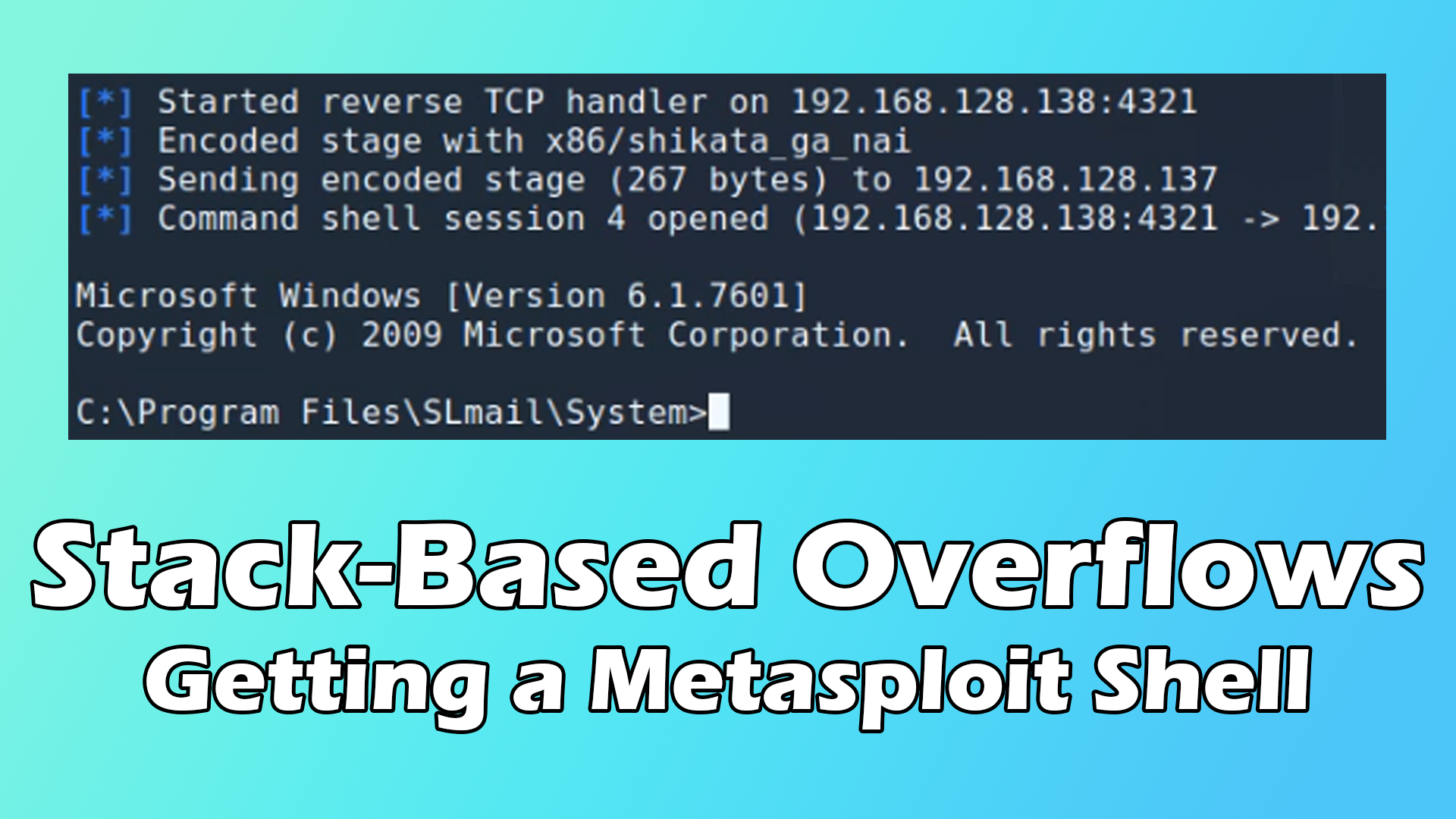
In this video I show how to recreate the popular SLMail exploit from scratch!
This video is the first part of a mini-series, so within the next couple of days the next video should be ready and published.
Exploit: https://www.exploit-db.com/exploits/638
Vulnerable Software: https://www.exploit-db.com/apps/12f1ab027e5374587e7e998c00682c5d-SLMail55_4433.exe (This software is intentionally vulnerable and should only be installed inside a virtual machine. In order to recreate the exploit as shown in this video, you will need to use a 32-bit Windows 7 installation. Windows Vista or XP may work as well.)
Windows 7 Virtual Machine: https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
Kali Linux: https://kali.org (https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/)
VMware: https://www.vmware.com/dk/products/workstation-player/workstation-player-evaluation.html (You may be able to use VirtualBox as well.)
Immunity Debugger: https://www.immunityinc.com/products/debugger/
Mona: https://github.com/corelan/mona (https://github.com/corelan/mona/archive/master.zip)
Python: https://www.python.org/downloads/release/python-2717/ (https://www.python.org/ftp/python/2.7.17/python-2.7.17.msi)
Background real space image: https://hubblesite.org/image/3862
POC: https://pastebin.com/KP7Qr0kb
Final POC: https://pastebin.com/qgZvaTVY
Topics covered:
– Installation of tools inside the Windows 7 virtual machine
– Adding a network interface to the virtual machine
– Kali Linux Undercover Mode
– Python POC Basics (Explaining the Proof Of Concept)
– Verifying that our SLMail service is running
– Changing the appearance (i.e. font size) of Immunity Debugger
– Overflowing the Extended Instruction Pointer (EIP)
– Sending a controlled crash string to modify EIP
– Searching memory for “opcodes” in loaded modules such as DLLs (Multiple ways)
– Little Endian encoding of EIP
The remaining topics such as finding bad characters, generating shellcode, reconfiguring the windows firewall, etc., will be covered in the following video.
Stay tuned and subscribe for more upcoming videos showing actual hacks!
Twitter: @CrazyDaneHacker
Facebook: https://www.facebook.com/crazydanishhacker
Patreon: https://www.patreon.com/crazydanishhacker

Recent Comments