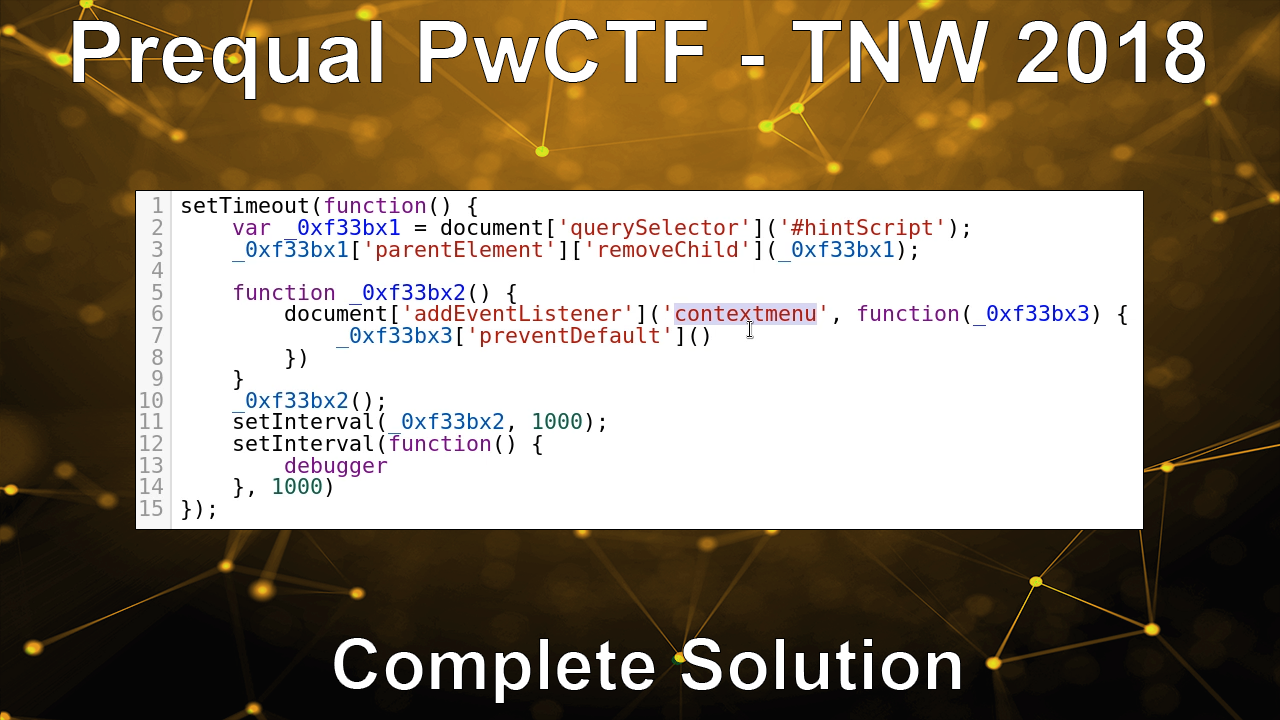
Description
In this video I demonstrate how to obtain the flag from a compiled Python file. (PYC)
Update: The challenges in this CTF were developed by the PwC Team in Israel. CTFd.io was only used as the base platform.
Disclaimer: Explicit written permission should be obtained if you are going to test a system that you do not legally own. A lot of websites have a “bug bounty program” these days, which allow you to test websites of big companies, as long as you follow their pentest engagement rules. (Refer to e.g. HackerOne)
Special Thanks:
– Josh (First elite supporter!)
Tools:
– VMware (https://www.vmware.com/go/downloadplayer)
– Kali Linux (https://kali.org)
– PyCharm (https://www.jetbrains.com/pycharm/)
– Xlate (https://paulschou.com/tools/xlate/)
Stay tuned and subscribe for upcoming video about various types of hacks!
Twitter: @CrazyDaneHacker
Facebook: https://www.facebook.com/crazydanishhacker
Patreon: https://www.patreon.com/crazydanishhacker

Great solution demonstration mate & I’m happy you liked our PwCTF challenge 😉